|
The All Hazards Consortium is working with the U.S. Department of Homeland Security and the Johns Hopkins Applied Physics Laboratory to determine prioritized cyber security requirements across multiple sectors including energy (electric), food, fuel, healthcare/life sciences, and transportation
The initial focus will be in the Identity Management and Data Privacy cyber areas. This cyber initiative will leverage the private sector stakeholders of the AHC and its Multi-State Fleet Response Working Group, key technical experts in cyber security, and a private sector operated trusted framework for information sharing called the SISE (Sensitive Information Sharing Environment) to: 1) identify common themes within cyber security 2) prioritization of common threats and 3) validation from this user community that addressing these themes/threats would solve key use cases within their environments Initial deliverables of the initial efforts are:
|
|
Mission Areas
Disaster Management Sensitive Information Sharing Cyber Security R&D Into Market Fusion Center Integration |
Technologies
Drones / UAS/ UAVs Block Chain Technology App Development FirstNet Cyber Data Casting w/Digital TV Disaster Solutions
Common Operating Picture US/Canadian Border Crossing Guide Transportation STORM Central Website ROADS Central App E-ZPass Toll Station Guide Disaster App Store COMING SOON |
|
|
Identity Management
Identity Management (IdM) deals with identifying and managing individuals within a government, state, local, public, or private sector network or enterprise. In addition, authentication and authorization to access resources such as facilities or, sensitive data within that system are managed by associating user rights, entitlements, and privileges with the established identity.
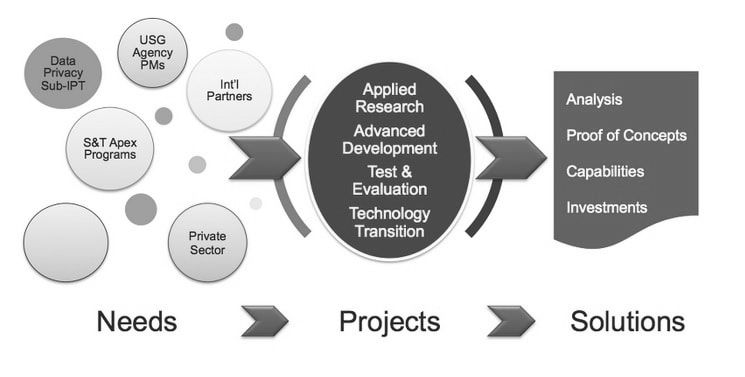
The question, “How do I know you are who you say you are and by what authority are you allowed access?” is, in part, a description of what IdM activities are trying to resolve. The mission of the IdM research projects is to develop, test, and evaluate interoperable tools, technologies, standards, and protocols for the purpose of controlling user access within and outside of organizational boundaries. Goal: Engage customer community, update and focus our research and development agenda & investments to develop solutions that address customer needs and have them be deployed and used operationally via successful technology transitions. More info..... https://www.dhs.gov/science-and-technology/csd-idm |
Data Privacy
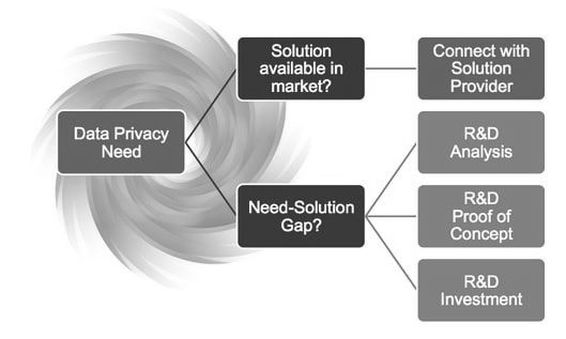
The DHS Data Privacy project develops, tests and evaluates tools and standards for the following:
It is working to ensure the protection of personal information consistent with public policy. The program regularly engages with our customers and the community to identify customer needs that cannot be met with current technologies, and to understand the current state of the art and practice in the data privacy domain. As a R&D program, DHS is actively "looking around corners" to ensure our customers are not surprised by emerging trends or emerging issues in the future. In cases where technologies do not exist or are immature, the program makes the necessary investments in applied research, advanced development, test and evaluation, and technology transition to ensure their availability to the Homeland Security Enterprise. Goal: Engage customer community, update and focus our research and development agenda & investments to develop solutions that address customer needs and have them be deployed and used operationally via successful technology transitions. More info..... https://www.dhs.gov/science-and-technology/csd-privacy |